By Denny Wan and Michael Collins
Peer reviewed by Jack Jones
Summary:
APRA CPS 234 requires that business Boards of regulated entities ensure their information security capability is commensurate with the size and extent of threats against their information assets, ensuring their continued sound operations. The assessment of whether the capability is commensurate with threats should be evaluated in accordance with the entity’s risk appetite for cyber risk. Often, risk appetite statements are high level business directives, qualitative in nature and require subjective interpretation in an operational context in order to develop measurements and metrics to support the assessment process. This paper presents an approach for estimating acceptable financial loss based on selected risk appetite statements. This methodology integrates cyber risk management into enterprise risk management by using the measurement in the reduction of financial loss as a common language which overcomes the inherent flaws in qualitative methods.
APRA CPS 234
The Australian Prudential Regulation Authority (APRA) is an independent statutory authority that supervises institutions across banking, insurance and superannuation and promotes financial system stability in Australia. APRA Prudential Standard CPS 234 Information Security came into force on 1st July 2019. The standard requires the business boards of regulated entities to maintain an information security capability commensurate with the size and extent of threats to their information assets, ensuring their continued sound operations. Where information assets are managed by a related party or third party, the APRA-regulated entity must assess their information security capability of that party, commensurate with the potential consequences of an information security incident affecting those assets.
This assessment process requires the dimensioning of the aforementioned capabilities and threats. An initial assessment can be performed by security audits, security solution reviews, system capacity reviews, simulated incident handling exercises, Disaster Recovery (DR) and Business Continuity Plan (BCP) development. Dimensioning can be performed using recognised standards for cyber risk quantification such as the Open Group FAIR (Factor Analysis of Information Risk) framework.
Armed with quantified measurements of information security capabilities and threats, assessment can be performed on commensurability. The FAIR framework can be used to estimate the expected reduction in risk (measured by the potential financial loss against the protected information asset) against the expected threat. The FAIR methodology is developed recognising that threat events appear to be random in terms of frequency of attack, probability of a successful attack and resulting financial loss. Therefore, the expected loss from a successful attack and the capability of the security solutions in reducing the expected loss is best expressed in the form of a Loss Exceedance Curve (LEC). The true average of the expected loss and reduction in expected loss are presented by the Confidence Intervals (CI) in the LEC.
Acceptable risk
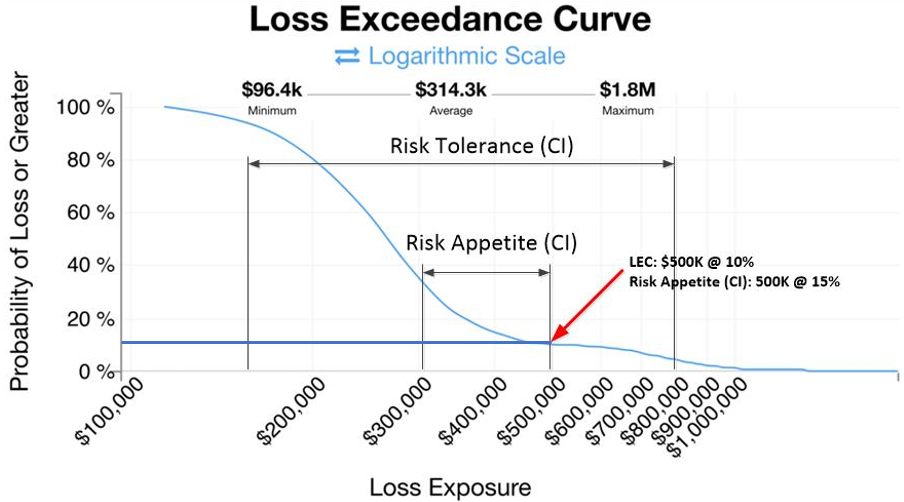
Understanding that there is no perfect security solution, investments in security capabilities can be expected to minimise but not totally eliminate expected losses. Ideally expected losses should fall within a range of business agreed parameters being an entities risk appetite and risk tolerance. The cost effectiveness of these investments is expected to level out with an increasing level of investment as shown in figure 1 below:

Figure 1: Dimensioning residual risk against risk appetite and risk tolerance limits
The LEC in figure 1 represents the residual risk after security controls have been applied. If the level of residual risk is within the risk appetite, the security control is sufficient and is part of normal business practice.
Typical risk appetite statements are high level business statements such as “we will not expose more than x% of our capital to losses in a certain line of business”. These high-level statements can be broken down into two key parameters: risk appetite and risk tolerance. Risk appetite represents the limit for “acceptable risks” under normal operating conditions. Risk tolerance defines the maximum deviation from the risk appetite. If the expected loss exceeds the risk tolerance, other risk transfer or mitigation strategies should be deployed to reduce the expected loss. Taken together, these two parameters serve as guard rails to protect the business from exposure to extreme risks which can reduce profitability and even lead to failure of the organisation.
To determine whether the security capability is sufficient, the risk appetite and risk tolerance levels should be compared against the LEC of the treated risk process after applying the security control. To facilitate such comparison, the risk appetite and risk tolerance levels must be expressed in the equivalent LEC format by solicitating risk appetite input from the risk owners and other key risk stakeholders and, quantifying these inputs using the FAIR methodology. The Australian Government Department of Finance issued a ten step guideline on how to define risk appetite and tolerance. The process involves interviewing senior executives to define the risk appetite statement and Subject Matter Experts (SMEs) to build and refine risk tolerance statements. These inputs capture the targeted risk range (risk appetite) and operational limits (risk tolerance).
To simplify visual representation, the approved risk appetite and risk tolerance CI, expressed as loss magnitude and probability value pairs, are marked against the LEC in figure 1. If these CI value pairs are greater than the expected losses at the corresponding part of the LEC, the solution is acceptable. For example, in figure 1 the probability of suffering a $500,000 loss is 10%. The risk appetite estimated a 15% probability of suffering this level of loss. Therefore, the residual risk level is acceptable. It can be concluded from this calculation that the information security capability is commensurate with the size of the threat.
John Wheeler (Gartner Global Research Lead on Integrated Risk Management spoke of the paradigm shift of “Techquilibrium” in his keynote in the recent FAIR Conference 2019. The focus is not on loss minimisation but to take good risks (measured by risk appetite) to make better decisions, to achieve new levels of growth through digital transformation.
The focus is not on loss minimisation but to take good risks (measured by risk appetite) to make better decisions, to achieve new levels of growth through digital transformation.
Risk appetite
The Bank of International Settlements guidance on “Principles for Sound Management of Operational Risk” provides some concrete examples on the application of the concept to operational risk management. The challenges in mapping high level risk appetite statements to operational risk management threshold were discussed in the PwC paper “Operation Risk Appetite”. The paper explored the process to propagate risk appetite statements from the business Board to the operational decision-making levels in the organisation.
The risk appetite of an organisation defines the boundary of its risk management framework. The Institute of Risk Management (IRM) paper “Risk Guidance Paper Appetite & Tolerance” identified the following principles for developing a risk appetite:
- It can be complex and should not be oversimplified for simplicity’s sake
- It needs to be measurable. Otherwise, the statement may become empty and vacuous. Shareholder value or ‘Economic Value Added’ may be a good starting point. Relevant and accurate data is vital to ensure this process subjects to the same level of data governance as routine accounting data.
- It is not a single fixed concept but consists of a range of appetites for different risks which might vary over time.
- It should be developed in the context of an organisation’s risk management capability, which is a function of risk capacity and risk maturity.
- It takes into account different views at strategic, tactical and operational levels.
- The control culture of the organisation at the operational level should be balanced against the propensity to take risks at the strategic level.
The IRM case study on risk appetite statements extracted from the annual reports of major companies explores how effective these six principles have been when applied and the lessons learned.
The importance of taking risk
Taking risk is essential to sustain profitable earnings in a competitive market. Without taking these risks, profit will be squeezed out by price competition. Outsourcing and other supply chain arrangements offer organisations opportunities to transfer risk at a better price than they can manage themselves. This allows organisations to focus on managing risks which give them a competitive advantage.
Taking risk is essential to sustain profitable earnings in a competitive market. Without taking these risks, profit will be squeezed out by price competition.
Therefore, both risk appetite and risk tolerance are inextricably linked to the performance of the business over time. These parameters, represented by the 95% CI estimates, are overlaid on the loss exceedance in figure 1 to highlight the information security – threat commensurability assessment.
If the probability of the expected loss is within the estimated risk appetite CI limits for the business, it can be concluded that security capability is commensurate with threats. Otherwise, the security controls should be reviewed and improved to reduce the expected loss, lowering it within the risk appetite CI. Similarly, if the CI estimate for the risk tolerance has been exceeded, other risk transfer mechanisms such as cyber insurance should be considered in order to narrow the gap.
Building an APRA CPS 234 compliance template
This section describes a generic APRA CPS 234 compliance template depicted in figure 2. The template measures residual risk to assess whether it is within the risk appetite, demonstrating that security capability remains commensurate with threats.

Figure 2 – A generic APRA CPS 234 compliance template
The template consists of three key steps:
- Apply risk appetite statements relevant to the key business process to be protected.
- Using the FAIR analysis framework calculate LEC and overlay this with the relevant risk appetite statements for the key business process.
- Perform FAIR analysis on the current and proposed security capabilities. The measurement is compared against the quantified risk appetite and risk tolerance levels in order to assess whether the capability is commensurate with threats.
These steps integrate cyber risk management into enterprise risk management by using the measurement of the reduction in financial loss as a common language. This language bridges the communications gap between the enterprise risk and cyber risk teams, enabling cyber risks to be managed consistently with other business risks and subjecting them to the same prudent financial management discipline based on ROI. These analyses provide the context to develop the effectiveness measurement metrics discussed in “Targeting cyber security investment – the FAIR approach”.
This language bridges the communications gap between the enterprise risk and cyber risk teams, enabling cyber risks to be managed consistently with other business risks and subjecting them to the same prudent financial management discipline based on ROI.
These risk processes are analysed using the Open Group FAIR methodology to extract the FAIR Factors and estimate their capability in reducing potential financial loss. The “Know Your Customer” (KYC) business process will be used to illustrate this three step process. This business process is supported by the risk processes including user identity and authentication management.
Step 1
The Enterprise Risk Management (ERM) and Information Security (infosec) team jointly review the collection of risk appetite statements to identify statements applicable to the key business process. For the KYC process, an applicable risk appetite statement might be:
Management is willing to accept non-exceptional operational risk event losses to a maximum of x% of revenue due to identity fraud.
This risk appetite statements could influence the selection of a new user identity solution for online banking channels. The user identification process is a key assurance process for Anti-Money Laundering (AML) compliance and a potential barrier to scaling these services. A tiered identity solution might be considered where lower assurance level of the identity capturing process is tolerated for accounts with lower limits on the frequency and amount of transactions. For accounts with higher transaction limits, solutions with a higher level of assurance, such as in-person verification process, might be mandated. In the Australian context, some Buy Now Pay Later (BNPL) financial services providers only require their users to validate their ownership of a credit or debit card issued by other financial institutions. This identity proofing approach reduces the cost of its identity management solution and improves the speed of approving new customers.
Step 2
The risk appetite statements selected in step 1 are then applied to the key risk processes to create the scenario for FAIR analysis. At this analysis stage, proposed security solutions are not considered in the modelling. In other words, this phase of the analysis measures the inherent risks of these processes. As suggested in the Department of Finance guidelines to develop risk appetite, senior management such the Chief Risk Officer (CRO), heads of line-of-business and operations teams are invited to provide expert estimates for FAIR analysis. The FAIR methodology use the PERT distribution to model expert opinions. The PERT distribution is well suited for this task because it only requires an estimate on the minimum, maximum and most likely values. It does not require a historical loss value for this phase of the analysis. The output from this analysis phase calculates risk appetite and risk tolerance CI values as inputs for step 3. If risk appetite and risk tolerance levels are currently expressed in heatmap format, they can be mapped into CI (expressed in the form of LEC) using this analysis step.
Step 3
This analysis phase estimates the capability of proposed new security controls in reducing potential financial loss against the protected information asset in the key business process should the previous step identify that the current state (inherent) fall outside the business risk tolerances. The goal of this analysis step is to assess whether information security capability is commensurate with threats by comparing the residual risk (after applying the security controls) with the risk appetite CI.
For the KYC process, the information asset is the assurance level of the authenticity of the user identity. Failure in this control can expose the organisation to regulatory actions under their AML compliance obligations. If multiple security control options are available, the cost effectiveness of these options can be compared by estimating the Return on Security Investment (ROSI) for each option and their corresponding maturity profile
The FAIR factor analysis and measurement metrics are summarised in the ROSI Scorecard depicted in figure 3. Most security controls require integration with business processes and infrastructure. These integration processes can take some time to mature. The maturity process can be tracked via the ROSI Maturity Dashboard shown in figure 2. Appendix-H in APRA CPG 234 (implementation guide for CPS 234) includes some suggestions on common information and metrics to be reported to the board. These are useful inputs to the composition of the scorecard and dashboard.
Trade-offs between ROSI and time to mature the solution can be evaluated based on these calculations. Security controls with a lower ROSI but shorter time to mature which minimise expected losses while waiting for maturation might be preferred.

Figure 3 – ROSI Scorecard format
Conclusion
The APRA CPS 234 Information Security standard has put cyber risk firmly as a business risk demanding attention and accountability from the business Boards of regulated entities. Boards are required to ensure information security capability is commensurate with threats. This approach demands a structured approach to the measurement of capability and threat and ensures the defensibility of the business approach to demonstrating this. The Open Group FAIR cyber risk quantification framework is a suitable tool for this measurement process.
Moreover, this measurement process can also be used to provide an estimate of the residual risk limits. Residual risk exists because no solution can completely eliminate threats. This is because the cost effectiveness of a security solution levels off once it has exceeded the optimal investment level. In fact, accepting a degree of residual risk is often part of the design of the security solution in order to lower the total investment provided it is within the risk appetite limits.
Residual risk is compared against the organisational risk appetite for the key business process. If the residual risk is less than the risk appetite and risk tolerance limits, the entity can conclude that its security capability is commensurate with the threat. Otherwise, it should review and improve its capabilities to ensure compliance.
About the authors:
Denny Wan is a cyber security expert with over 20 years experience in the Australian IT security sector. He is the principal consultant of Security Express and the chair of the Sydney Chapter of the FAIR Institute with deep expertise in Cyber Risk Economics. FAIR is an effective approach for prioritising cyber security investments and explaining its business values. He is a certified PCI QSA and CISSP. He is a postgraduate researcher at the Optus Macquarie University Cyber Security Hub researching into cyber risk management in the supply chains. This research is a useful tool for managing 3rd party supplier risks under compliance frameworks such as APRA CPS 234.
Michael Collins is a Cybersecurity and Digital Risk Management executive passionate about establishing and promoting quantitative methods for analysing information security risk which assists business partners, executives and board members in achieving the right balance between protecting the organisation and achieving business outcomes. Michael is currently leading the Cybersecurity capability at HESTA, Australia’s leading Health and Community sector industry superannuation fund with over 840,000 members and $50Bn funds under management.
About the reviewer:
Jack Jones is a thought leader in risk management and information security earning him the 2006 ISSA Excellence in the Field of Security Practices award, and the 2012 CSO Compass Award for Leadership in Risk Management. He created the Factor Analysis of Information Risk (FAIR) cyber risk quantification framework published by the Open Group since 2009. FAIR has seen adoption globally, within organizations of all sizes, and is now regularly included in graduate-level university courses on information security and referenced by other industry standards. His co-authored book on FAIR entitled “Measuring and Managing Information Risk – A FAIR Approach“, has been inducted into the Cybersecurity Canon as a “must read” for professionals in the industry. He is the Chief Risk Scientist at RiskLens which has developed the only cyber risk management software purpose-built on FAIR, the international standard quantitative model for cybersecurity and operational risk. Jack is also the Chairman of The FAIR Institute, a non-profit organization led by information risk officers, CISOs and business executives to develop standard information risk management practices based on FAIR.
Find the original article here: https://www.linkedin.com/pulse/building-apra-cps-234-compliance-template-denny-wan/

